Instructions
Objective
Write a program in MASM that allows you to encode and decode messages with simple substitution cypher assignment solution.
Requirements and Specifications
Objectives
- Working on a project that utilizes a broad spectrum of knowledge from this course
- Using various forms of indirect addressing
- Passing parameters on the stack
- Extensive interaction with arrays
Description:
Alex and Sila are espionage agents working for the Top Secret Agency (TSA). Sometimes they discuss sensitive intelligence information that needs to be kept secret from the Really Bad Guys (RBG). Alex and Sila have decided to use a simple obfuscation algorithm that should be good enough to confuse the RBG. As the TSA’s resident programmer you’ve been assigned to write a MASM procedure that will implement the requested behavior. Your code must be capable of encrypting and decrypting messages (and meet the other requirements given in this document). This final project is written less like an academic assignment and more like a real-life programming task. This might seem daunting at first but don’t despair! Algorithm Details Ankur and Sila’s algorithm is a simple substitution cipher. If you are not familiar with substitution ciphers, I suggest reading the Wikipedia page (available here: Links to an external site.). For this implementation, the key consists of 26 lowercase English letters. The following example demonstrates the obfuscation algorithm that Ankur and Sila are requesting. Suppose that you are provided the following 26 character secret key: efbcdghijklmnopqrstuvwxyza. Each character listed in the key corresponds to a character from the English alphabet. In other words, the key is a map that tells you how to take the original text (also known as plaintext) and replace each letter with the encrypted character. In order to understand the key, consider the alphabetical arrangement of the English alphabet beginning with a, b, c, d, e, f, (and so on). Now reconsider the key, which starts with e, f, b, c, d, g, (and so on).
Screenshots of output
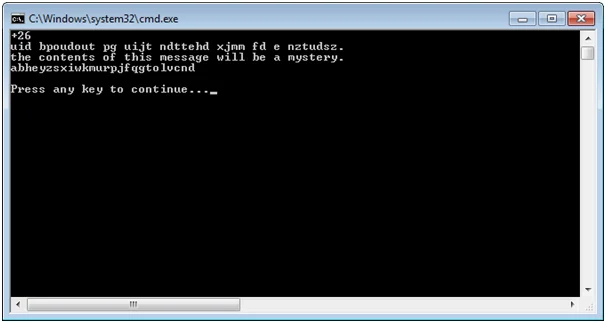
.webp)
Source Code
Computer.asm
INCLUDE Irvine32.inc
.code
;------------------------------------------
compute PROC
;
; Computes the operation given as argument
; Receives: for the decoy mode:
; 16 bit signed WORD operand
; 16 bit signed WORD operand
; 32 bit OFFSET of a signed DWORD
; For the encryption mode:
; 32 bit OFFSET of a BYTE array
; 32 bit OFFSET of a BYTE array
; 32 bit OFFSET of a signed DWORD
; For the decryption mode:
; 32 bit OFFSET of a BYTE array
; 32 bit OFFSET of a BYTE array
; 32 bit OFFSET of a signed DWORD
; For the key generation mode:
; 32 bit OFFSET of a BYTE array
; 32 bit OFFSET of signed DWORD
; Returns: nothing
;------------------------------------------
push ebp
mov ebp, esp
push ebx
mov ebx, [ebp + 8] ; load dest address
cmp DWORD PTR [ebx], -1 ; check selected mode
je callEnc ; if -1, encrypt
cmp DWORD PTR [ebx], -2 ; check selected mode
je callDec ; if -2, decrypt
cmp DWORD PTR [ebx], -3 ; check selected mode
je callGen ; if -3, generate
; else, use decoy mode
mov ax, [ebp + 12] ; pass numbers to procedure
push ax
mov ax, [ebp + 14]
push ax
call addNumbers ; add numbers
add esp, 4 ; remove args from stack
mov [ebx], eax ; save result
jmp compRet
callEnc:
mov eax, [ebp + 16] ; pass pointers to procedure
push eax
mov eax, [ebp + 12]
push eax
call encrypt ; encrypt message
add esp, 8 ; remove args from stack
jmp compRet
callDec:
mov eax, [ebp + 16] ; pass pointers to procedure
push eax
mov eax, [ebp + 12]
push eax
call decrypt ; decrypt message
add esp, 8 ; remove args from stack
jmp compRet
callGen:
call Randomize
mov eax, [ebp + 12] ; pass pointer to procedure
push eax
call generateKey ; generate key
add esp, 4 ; remove arg from stack
compRet:
pop ebx
pop ebp
ret
compute ENDP
;------------------------------------------
addNumbers PROC
;
; Calculates the sum of two signed WORD numbers
; Receives: two signed WORD arguments in the stack
; Returns: sum of the two numbers in eax
;------------------------------------------
push ebp
mov ebp, esp
push ebx
movsx eax, SWORD PTR [ebp + 8] ; load first number
movsx ebx, SWORD PTR [ebp + 10] ; load second number
add eax, ebx ; return sum
pop ebx
pop ebp
ret
addNumbers ENDP
;------------------------------------------
encrypt PROC
;
; Encrypts the message passed as argument using the
; given key
; Receives: two string addresses in stack
; Returns: nothing
;------------------------------------------
push ebp
mov ebp, esp
push esi
push edi
mov esi, [ebp + 12] ; load key pointer
mov edi, [ebp + 8] ; load message pointer
mov eax, 0
encLoop:
mov al, [edi] ; load char from message
cmp al, 0 ; if end of string
je encRet ; terminate
cmp al, 'a' ; see if it's a letter
jl encSkip ; if not, do not encrypt
cmp al, 'z' ; see if it's a letter
jg encSkip ; if not, do not encrypt
sub al, 'a' ; convert to 0-25
mov al, [esi + eax] ; load encrypted char
mov [edi], al ; save encrypted char
encSkip:
inc edi ; advance to next char in message
jmp encLoop
encRet:
pop edi
pop esi
pop ebp
ret
encrypt ENDP
;------------------------------------------
decrypt PROC
;
; Decrypts the message passed as argument using the
; given key
; Receives: two string addresses in stack
; Returns: nothing
;------------------------------------------
push ebp
mov ebp, esp
push esi
push edi
mov esi, [ebp + 12] ; load key pointer
mov edi, [ebp + 8] ; load message pointer
mov eax, 0
decLoop:
mov al, [edi] ; load char from message
cmp al, 0 ; if end of string
je decRet ; terminate
cmp al, 'a' ; see if it's a letter
jl decSkip ; if not, do not decrypt
cmp al, 'z' ; see if it's a letter
jg decSkip ; if not, do not decrypt
mov ecx, 0 ; find letter in key
find:
cmp al, [esi + ecx] ; see if we found the letter in the key
je found ; if so, end
inc ecx ; advance to next char
jmp find
found:
add cl, 'a' ; convert position to ascii
mov [edi], cl ; save decrypted char
decSkip:
inc edi ; advance to next char in message
jmp decLoop
decRet:
pop edi
pop esi
pop ebp
ret
decrypt ENDP
;------------------------------------------
generateKey PROC
;
; Generates a new key and saves it in the argument
; Receives: one string addresses in stack
; Returns: nothing
;------------------------------------------
push ebp
mov ebp, esp
push edi
push ebx
push ecx
push edx
mov edi, [ebp + 8] ; load key pointer
; fill key with letters in order
mov ecx, 26
mov al, 'a'
fill:
mov [edi], al
inc edi
inc al
loop fill
mov edi, [ebp + 8] ; reload key pointer
; shuffle 26 times
mov ecx, 26
shuffle:
; generate pair to exchange
mov eax, 26
call RandomRange
mov edx, eax
mov eax, 26
call RandomRange
; save old chars
mov bl, [edi + eax]
mov bh, [edi + edx]
; swap them
mov [edi + eax], bh
mov [edi + edx], bl
loop shuffle
pop edx
pop ecx
pop ebx
pop edi
pop ebp
ret
generateKey ENDP
END
Main.asm
INCLUDE Irvine32.inc
EXTERN compute@0:PROC
compute EQU compute@0
.data
operand1 WORD 46
operand2 WORD -20
dest0 DWORD 0
myKey BYTE "efbcdghijklmnopqrstuvwxyza"
message BYTE "the contents of this message will be a mystery.",0
dest1 DWORD -1
dest2 DWORD -2
newKey BYTE 26 DUP(?)
BYTE 0
dest3 DWORD -3
.code
main PROC
push operand1
push operand2
push OFFSET dest0
call compute
add esp, 8
mov eax, dest0
call WriteInt
call CrLf
push OFFSET myKey
push OFFSET message
push OFFSET dest1
call compute
add esp, 12
mov edx, OFFSET message
call WriteString
call CrLf
push OFFSET myKey
push OFFSET message
push OFFSET dest2
call compute
add esp, 12
mov edx, OFFSET message
call WriteString
call CrLf
push OFFSET newKey
push OFFSET dest3
call compute
add esp, 8
mov edx, OFFSET newKey
call WriteString
call CrLf
call CrLf
call WaitMsg
exit
main ENDP
END main
Similar Samples
Explore our curated programming assignment samples at ProgrammingHomeworkHelp.com. From Java and Python to Assembly Language and SQL, each sample demonstrates our expertise in delivering precise solutions. Dive into our samples to see how we can assist you in mastering programming concepts and achieving academic success.
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
Assembly Language
